Bron: CrowdStrike, Tenable, Access42, NCSC
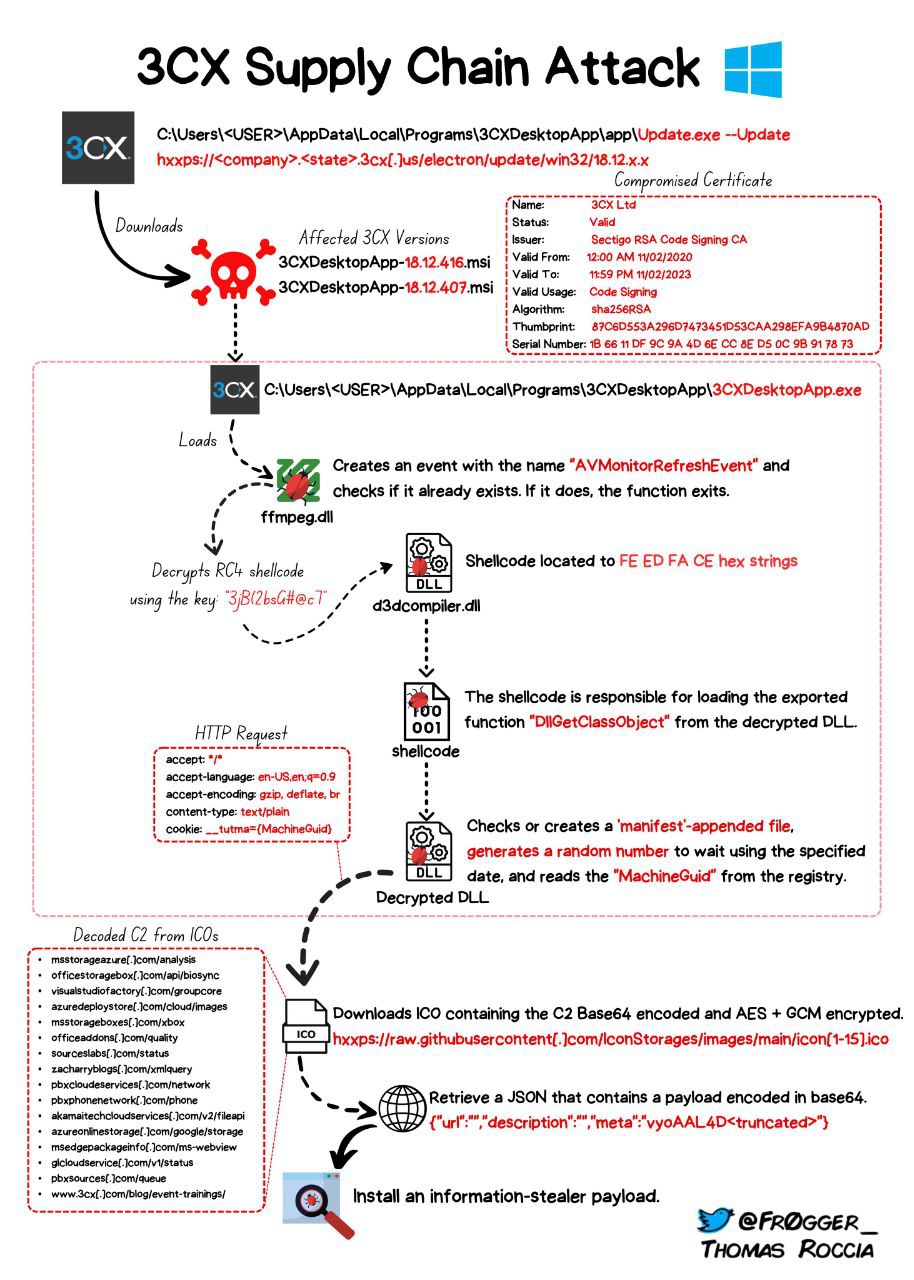
Op 29 maart 2023 observeerde Falcon OverWatch onverwachte kwaadaardige activiteit afkomstig van een legitieme, ondertekende binary, 3CXDesktopApp – een softphone applicatie van 3CX. De kwaadaardige activiteit omvat beaconing naar actor-gecontroleerde infrastructuur, inzet van second-stage payloads, en, in een klein aantal gevallen, hands-on-toetsenbord activiteit.
Weten we welke versies van de 3CX desktop apps kwetsbaar zijn?
Vanaf 29 maart, gebaseerd op wat publiekelijk is gedeeld door onderzoekers, worden de volgende versies van de 3CX desktop apps beschouwd als getroffen:
| Operating System | Version | Filename | SHA256 (Installer) |
|---|---|---|---|
| Windows | 18.12.407 | 3cxdesktopapp-18.12.407.msi | aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868 |
| Windows | 18.12.416 | 3cxdesktopapp-18.12.416.msi | 59e1edf4d82fae4978e97512b0331b7eb21dd4b838b850ba46794d9c7a2c0983 |
| macOS | 18.11.1213 | 3CXDesktopApp-18.11.1213.dmg | 5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290 |
| macOS | latest | 3cxdesktopapp-latest.dmg | e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec |
Op 30 maart publiceerde 3CX CISO Pierre Jourdan een blogpost met een lijst van extra getrojaniseerde 3CX desktop app versies voor macOS:
- 18.12.402
- 18.12.407
- 18.12.416
Wat doen deze getrojaniseerde versies van de 3CX desktop applicaties?
Onderzoekers melden dat de getrojaniseerde applicaties zijn waargenomen:
- Connecting back to infrastructure associated with the threat actors
- Retrieving and deploying “second-stage payloads”
- Hands-on-keyboard activity (limited cases)
Volgens nieuw bekendgemaakt onderzoek naar de aanval lijken de payloads van het tweede stadium te zijn gehost op een openbare GitHub-repository die sindsdien is verwijderd.
De payloads van het tweede stadium werden gebruikt om een informatiesteler van het derde stadium te downloaden, waardoor aanvallers informatie konden verzamelen zoals de browsergeschiedenis van populaire browsers zoals Google Chrome, Microsoft Edge, Brave en Mozilla Firefox.
Wat moet/kan je zelf doen?
- 3CX adviseert het softwareprogramma volledig te verwijderen indien update 7 op het systeem aanwezig is.
- Wanneer 3CX noodzakelijk is voor een vitaal proces binnen uw organisatie raden zij aan de webapplicatie te gebruiken.
- Access42 adviseert organisaties die gebruik maken van 3CX dringend dit advies op te volgen en na het verwijderen van de besmette update grondig onderzoek te doen binnen hun systemen.
- Access42 adviseert ook partijen die nog gebruikmaken van een oude(re) versie (update <7) expliciet ook onderzoek te doen naar mogelijke compromittatie van hun systemen en waakzaam te zijn op signalen van mogelijk misbruik.
CrowdStrike Falcon Detection and Prevention
Het CrowdStrike Falcon-platform beschermt klanten tegen deze aanval en heeft dekking met behulp van op gedrag gebaseerde aanvalsindicatoren (IOA’s) en compromisindicatoren (IOC’s) die gericht zijn op kwaadaardig gedrag in verband met 3CX op zowel macOS als Windows.
Klanten moeten ervoor zorgen dat het preventiebeleid correct is geconfigureerd met “Suspicious Processes” ingeschakeld. Onze managed klanten zijn inmiddels gecontroleerd.
Heeft Tenable plugins die klanten kunnen gebruiken om kwetsbare versies van de 3CX desktop applicatie te identificeren?
Tenable heeft drie plugins uitgebracht:
| Plugin ID | Plugin Name |
|---|---|
| 173712 | 3CX DesktopApp Malware |
| 173677 | 3CX Desktop App Local Windows Detection |
| 173679 | 3CX Desktop App Local macOS Detection |
Plugin ID 173712 kan worden gebruikt om de versies van 3CX DesktopApp te identificeren die getrojaniseerd zijn. Op dit moment brengen wij actief onze managed klanten op de hoogte over eventuele kwetsbare systemen.
Op 30 maart meldde 3CX de release van bijgewerkte versies van de 3CX DesktopApp voor Windows en macOS: versie 18.12.422. Voor meer informatie verwijzen we naar de 3CX blog post.
Meer informatie
- https://www.3cx.com/community/threads/3cx-desktopapp-security-alert.119951/
- https://www.ncsc.nl/actueel/nieuws/2023/maart/30/ncsc-waarschuwt-voor-supplychain-aanval-3cx
- https://www.tenable.com/blog/3cx-desktop-app-for-windows-and-macos-reportedly-compromised-in- supply-chain-attack
- https://www.crowdstrike.com/blog/crowdstrike-detects-and-prevents-active-intrusion-campaign-targeting-3cxdesktopapp-customers/
- https://tweakers.net/nieuws/208206/windows-app-zakelijke-voip-dienst-3cx-verspreidt-malware-na-supplychainaanval.html






